Portswigger XSS Lab 1 Reflected XSS into HTML context with nothing encoded
- Your Friendly Hacker
- March 17, 2025
- 3:29 pm
- No Comments
- 4 Min Read
Table of Contents
Introduction
Hi, I’m your friendly hacker. I will be solving the Lab 1 today.Basically in this lab we have to generate a pop up on a website to confirm that cross-site scripting can be reflected on the website into a HTML content box.
About the Lab
Reflected Cross-site scripting into HTML context with nothing encoded
Before we begin, we should read this information text provided by the Academy.
Link to the Lab –https://portswigger.net/web-security/cross-site-scripting/reflected/lab-html-context-nothing-encoded
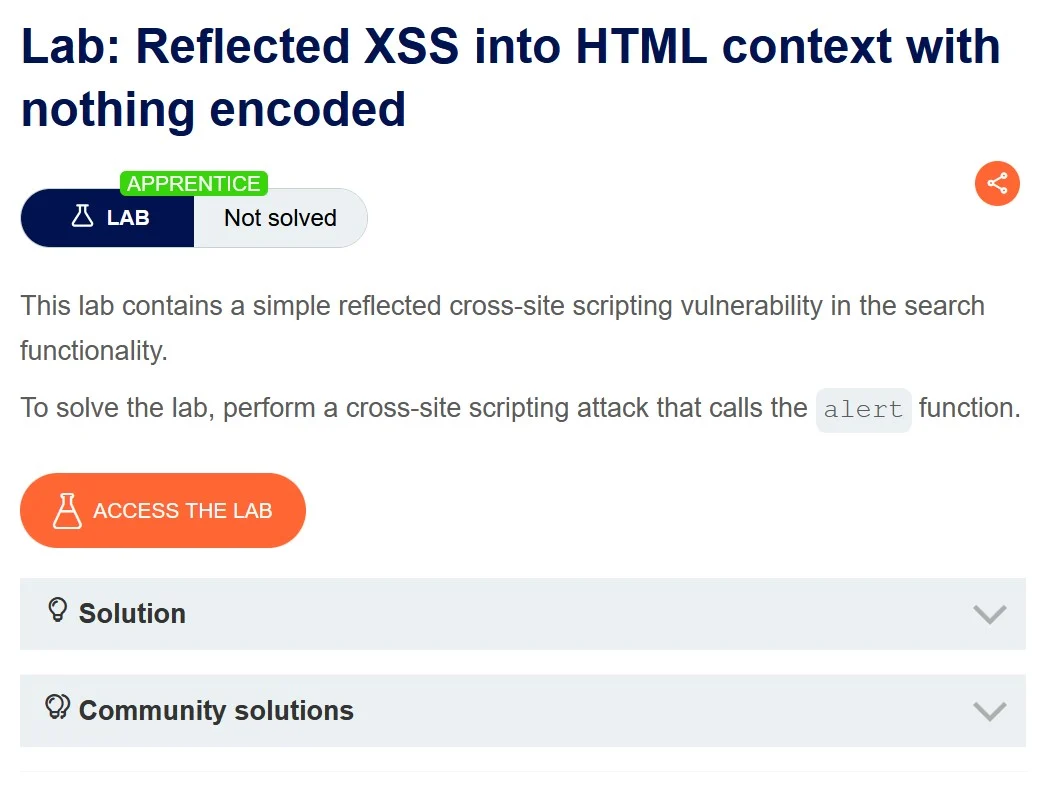
Once we go through the information provided. We are almost ready to start.
To start the lab we just have to click on the Access The Lab button.
Procedure
Open the Website
A soon as we Click on the Button , a blog Website starts loading on a new tab.
We will wait till the website gets loaded completely.

Looks like a Blog website, with a set of Blogs on different topics.
We need to look for something that can be of some use to us.
Look for clues
We can look for any field where we can give an input like the search bar.
Hey we do have a Search Bar on this website.
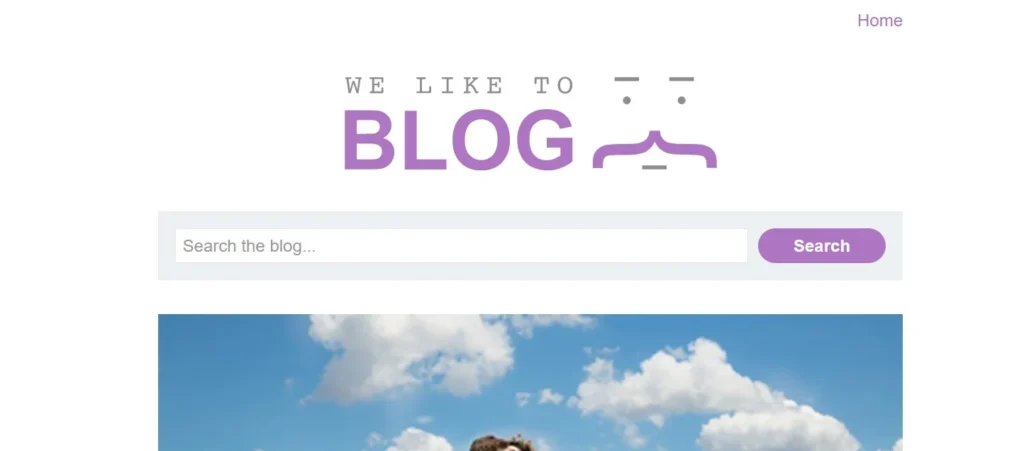
Play around with Search Bar
We will try to search something in the search bar.
I will go ahead and search for a “Bag”. Lets see what we get in reply.
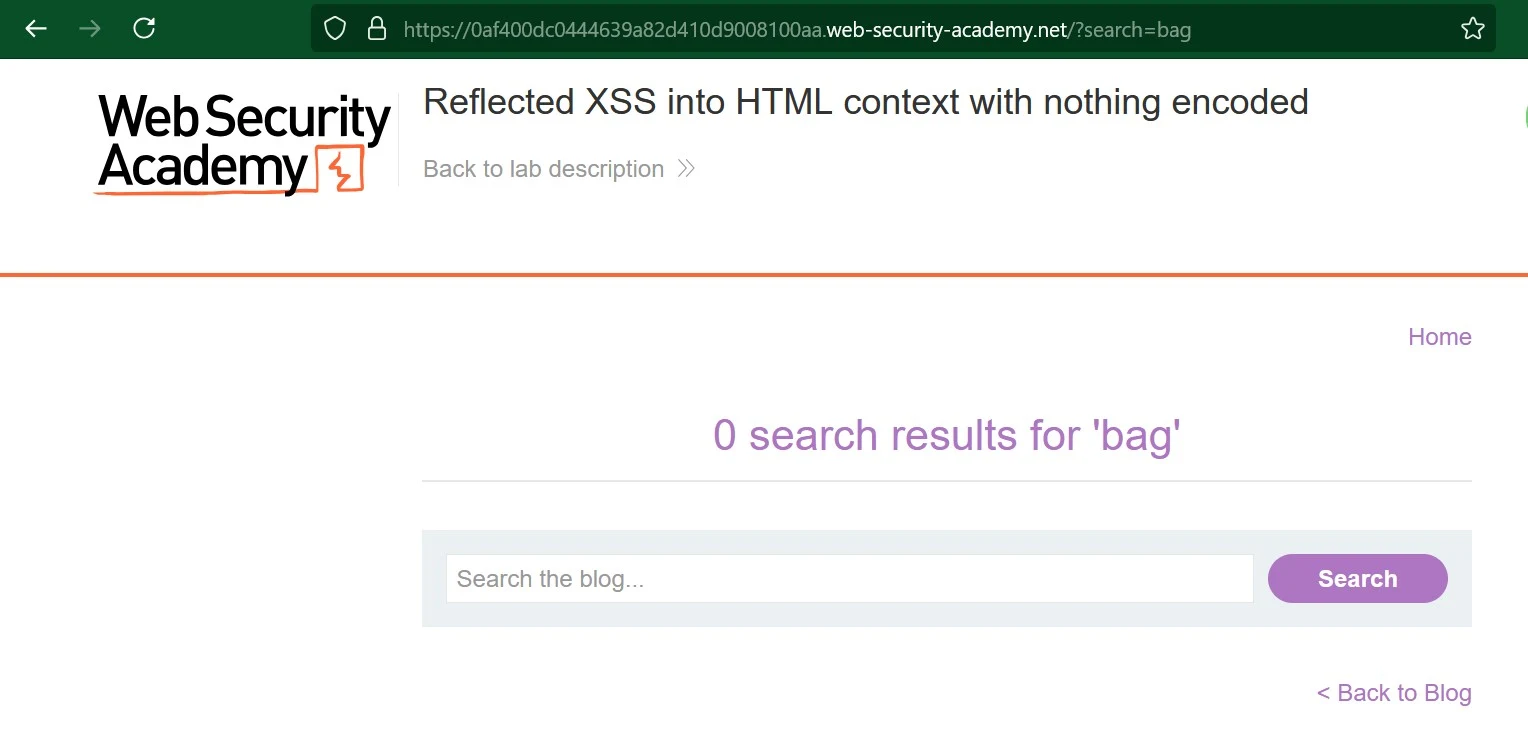
We Got 0 results for a Bag.
Check the Url
Lets check the url Link if we found anything of significance. I have posted the Link below:
https://0af400dc0444639a82d410d9008100aa.web-security-academy.net/?search=bag
We can observe in the url that ?search=bag. well that’s a GET Parameter.
Execute our code
So we will now try to execute a code by replacing bag with our own code to generate a pop up on the website.
we will type the following code in the url after search=
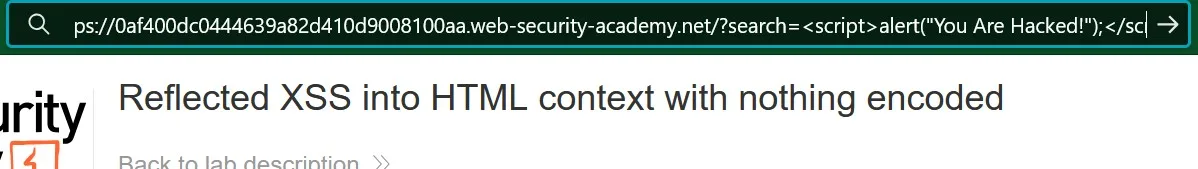
<script>alert("You Are Hacked");</script>
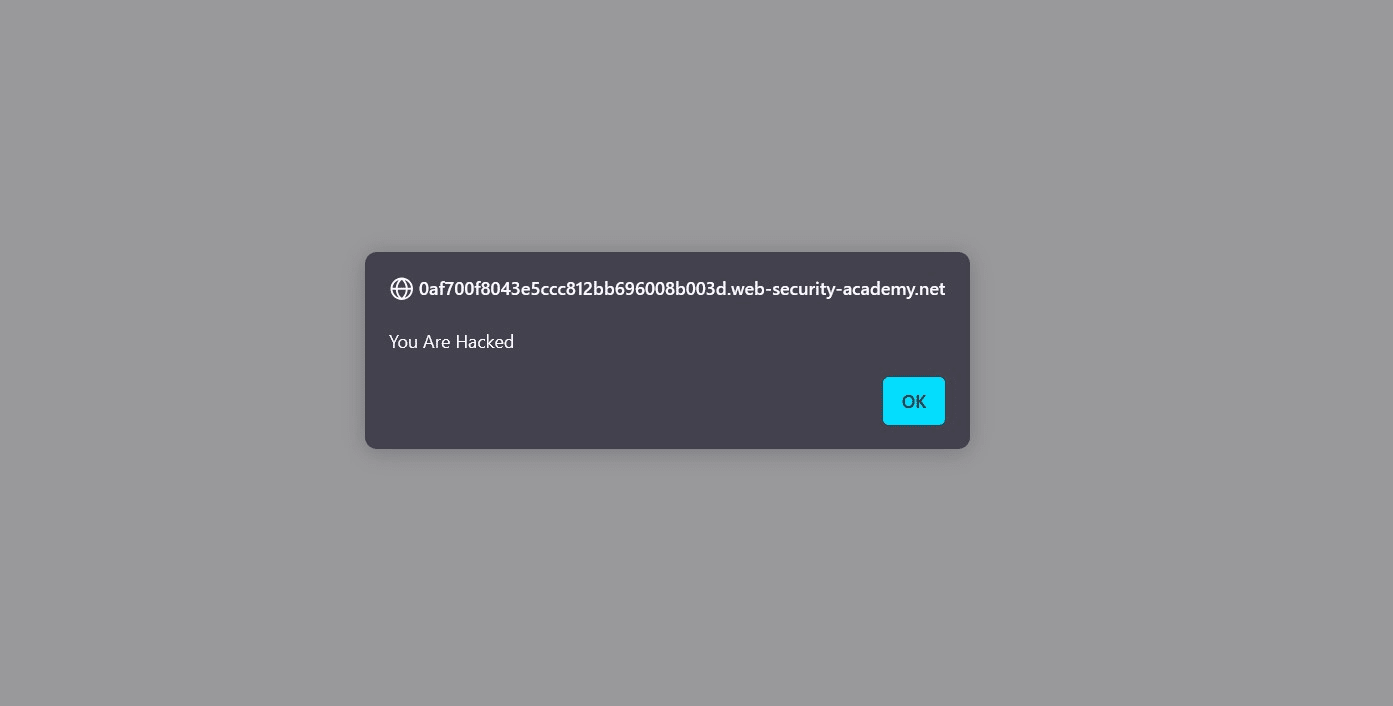
As soon as we executed the code in the browser.
XSS Attack is Successful
We got a pop up.which proves that the Blog website was vulnerable to a Cross site scripting Attack.
Tips & Tricks
The best practice is to compile your own Cross-site Scripting Payload for yourself.
A Cross-site Scripting Payload is very essential while trying to execute a Cross-Site Scripting attack. If you don’t know anything about how to compile. You can definitely get it on Google. Just google about it and explore.
Also i would like to appreciate the Portswigger team for giving us such lively Labs for practicing.
Conclusion
And to be precise, we just completed our 1st Lab titled Reflected Cross-Site Scripting into HTML context with nothing encoded.
Hope, you liked the article and got to learn something valuable to you.
If you are looking for similar content, you can my Medium Page to learn more : https://medium.com/@yfhackerinfo
Also, you can find more Write-ups here.
And feel free to comment down below, Positive or negative it will help me grow.
See you in my next article. Have a Great day.
Happy Hacking!
As an Amazon Associate,i earn from qualifying purchases.
Share it with Friends
Follow Me
Your Friendly Hacker
Categories
Use Coupon Code - YFH10
-
Cybersecurity Terminologies – eBook
E-BooksRated 5.00 out of 5₹299.00Original price was: ₹299.00.₹99.00Current price is: ₹99.00. Add to cart -
Ultimate Guide to Open Redirect Exploitation in Bug Bounty
Bug BountyRated 4.83 out of 5₹299.00Original price was: ₹299.00.₹99.00Current price is: ₹99.00. Add to cart


Your Friendly Hacker
Lets Secure the World
Join me on my journey to make the internet a safe place again.
Contact Form