What is Bug Bounty in Cyber Security? A Beginner’s Guide
- Your Friendly Hacker
- May 21, 2025
- 10:08 pm
- No Comments
- 4 Min Read
Table of Contents
Introduction
Cybersecurity is one of the fastest-growing industries in today’s digital world. As organizations increasingly rely on technology, the risk of cyber threats and vulnerabilities has grown substantially. To combat these risks, companies are turning to an innovative and collaborative approach known as bug bounty programs.
But what is bug bounty, and why is it gaining so much popularity?
In simple terms, a bug bounty is a reward offered by companies or organizations to ethical hackers — also known as security researchers — for discovering and responsibly reporting bugs or security flaws in their applications, websites, or systems. These programs not only help strengthen security but also offer skilled individuals a legal and rewarding way to put their hacking skills to good use.
With leading tech giants like Google, Facebook, Apple, and PayPal offering lucrative bounty programs, bug bounty hunting has evolved into a legitimate and often highly profitable career path. Whether you’re a student, a professional cybersecurity enthusiast, or someone curious about ethical hacking, learning what a bug bounty is and how it works is the first step toward making your mark in this exciting field.
In this post, we’ll cover:
What is bug bounty and how it works
Who offers bug bounty programs
How you can get started as a beginner
Tips, tools, and platforms for success
Let’s dive deep into the world of ethical hacking and discover how bug bounties can open up real opportunities for learning, earning, and growing in the cybersecurity space.

What is a Bug Bounty?
A bug bounty is a financial reward offered by companies to independent security researchers (a.k.a. bug bounty hunters) who find and report vulnerabilities in their systems. These programs allow organizations to fix issues before bad actors can exploit them.
Think of it like this:
You’re helping someone lock their doors — and getting paid for it.
Why Do Companies Offer Bug Bounty Programs?
- Proactive Security: Fix vulnerabilities before attackers find them.
- Cost-Effective: Pay only for results, not for full-time security staff.
- Global Reach: Access thousands of skilled researchers from around the world.
- Compliance & Trust: Demonstrates commitment to security and user safety.

How Much Can You Earn From Bug Bounty?
First we understood What is Bug Bounty. Bug bounties range from $50 to $100,000+ depending on:
- Severity of the vulnerability
- Scope of the program
- Company size (Google, Apple, Meta pay more)
Some top bounty hunters have earned over $1 million on platforms like HackerOne and Bugcrowd.
🧠 Real-Life Example
Google’s Bug Bounty Program has paid over $45 million to security researchers since 2010. The highest single bounty? $161,337 for a Pixel remote code execution bug!
Where to Find Bug Bounty Programs?
Tools You Need to Get Started
To be a successful bug bounty hunter, you’ll need these:
- 🧰 Burp Suite (Free and Pro versions)
- 🧰 Nmap – for scanning open ports
- 🧰 Amass / Subfinder – for reconnaissance
- 🧰 OWASP ZAP – for automated scanning
- 🧰 Kali Linux or Parrot OS – penetration testing OS

Best Courses to Learn Bug Bounty in 2025
Here are beginner-friendly online courses specially curated for you to make you understand what is bug bounty to advanced topics such as techniques to earn bug bounties:
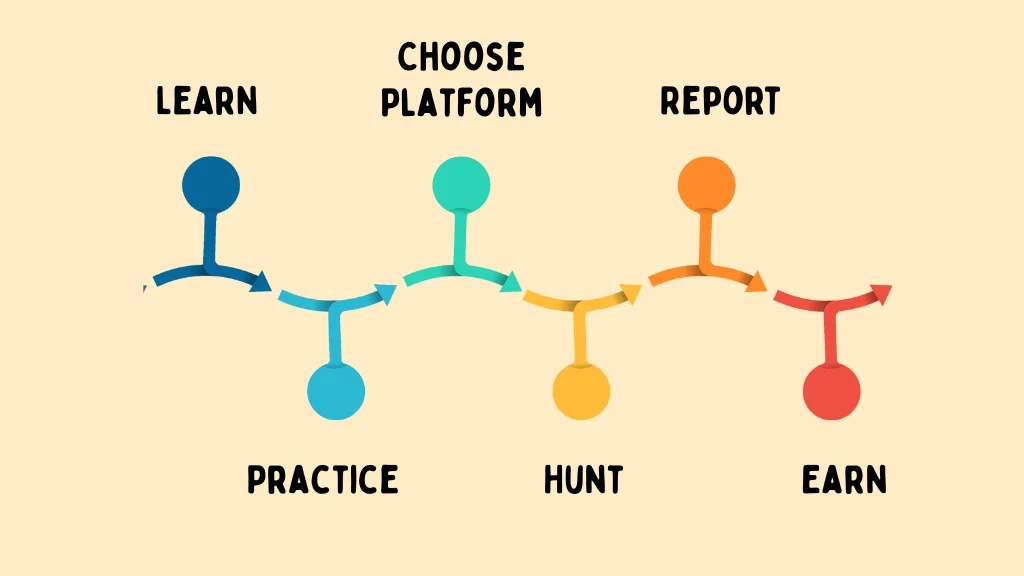
How to Start Bug Bounty Hunting (Step-by-Step)
Learn Basic Cyber Security
Begin your journey by understanding the fundamentals of cybersecurity. Start with networking concepts like TCP/IP, DNS, and HTTP/HTTPS protocols to know how the internet functions. Learn how servers and clients communicate, and how websites are structured. Pair this knowledge with Linux basics — since most hacking tools are built for Linux environments — and master command-line operations. Then, dive into the OWASP Top 10 list to familiarize yourself with the most common and critical web vulnerabilities, such as XSS, SQL Injection, and Broken Authentication. This foundation will help you identify and exploit real-world security flaws during your bug bounty journey.
Practice on Platforms
Before jumping into live programs, refine your skills using legal and beginner-friendly practice labs. Platforms like TryHackMe and Hack The Box offer guided paths for cybersecurity learners, including beginner to advanced rooms on penetration testing and web hacking. PortSwigger Web Security Academy is another free and powerful resource where you can practice real-world scenarios in-browser, including OWASP vulnerabilities, authentication bypasses, and business logic flaws. These environments help you build both confidence and skill in a risk-free, structured way. Next Step involves, understanding what is bug bounty platform.
Pick a Bug Bounty Platform
First Understand what is Bug Bounty. When you have understood what is Bug Bounty, you can go ahead with the Next steps. When you’re ready to go live, join reputable bug bounty platforms that host programs from companies across the globe. The most popular platforms include:
HackerOne – Known for large community support and beginner-friendly programs.
Bugcrowd – Offers public and private programs for all skill levels.
Intigriti – A fast-growing European platform that offers competitive rewards.
These platforms connect you with real-world programs from startups to Fortune 500 companies that pay you for discovering valid security issues.
Study Program Scope
Every bug bounty program has a defined scope and set of rules. This includes which domains, applications, and types of vulnerabilities are eligible for rewards. Always read and understand the program’s:
Scope (in-scope and out-of-scope assets)
Testing rules (rate-limiting, user data restrictions)
Reward criteria (how payouts are calculated)
This ensures you don’t waste time testing unqualified assets and keeps you compliant with the platform’s legal boundaries.
Hunt Ethically
Ethical hacking is the core of bug bounty. Never test applications or systems that are not part of the authorized scope. Doing so can result in disqualification, legal actions, or even permanent bans from platforms. Respect the rules, don’t exploit bugs beyond demonstration, avoid accessing sensitive data, and always use non-destructive payloads. Being ethical builds trust with companies and platforms and helps maintain the integrity of the bug bounty ecosystem.
Write Quality Reports
Finding a vulnerability is only half the job — reporting it clearly is equally important. A good bug report should:
Include step-by-step reproduction steps
List payloads or tools used
Explain the vulnerability’s impact
Include screenshots or proof-of-concept (PoC)
Suggest possible fixes (optional, but appreciated)
Quality reports not only increase your chances of getting rewarded but also help you stand out as a professional in the bug bounty community.
Ethics and Legality in Bug Bounty
Remember, bug bounty is legal only when done within authorized programs. Hacking outside scope — even with good intent — is illegal and can lead to prosecution.
Always stick to the rules provided by the company or platform.
Table
Final Thoughts
So now you know what is Bug bounty hunting in cyber security. It is not just a trend — it’s a powerful career path for anyone passionate about hacking ethically and getting rewarded for it. With the right tools, training, and platforms, you can go from beginner to pro in 2025.
Whether you’re a student, a hobbyist, or an aspiring cybersecurity professional — this could be your gateway into the industry.

💥 Check out these beginner-friendly bug bounty platforms:
👉 Sign up for HackerOne
👉 Join TryHackMe for bug bounty labs
👉 Explore Ethical Hacking Courses on Udemy
Frequently Asked Questions (FAQ)
A bug bounty program is an initiative run by organizations that rewards ethical hackers for finding and reporting security vulnerabilities in their applications or systems.
Ethical hackers look for security flaws in the scope of a bug bounty program. When they find one, they report it to the organization. If it’s valid, they are rewarded with money, swag, or public recognition.
Not necessarily. Many bug bounty hunters begin with basic knowledge of web vulnerabilities and gradually learn tools like Burp Suite, browser dev tools, and scripting as they progress.
Yes, as long as you participate in authorized programs on platforms like HackerOne, Bugcrowd, or Synack. Unauthorized hacking is illegal and can lead to serious legal consequences.
Earnings depend on the severity of bugs and the target’s bounty structure. Rewards can range from $50 to over $50,000 for critical bugs, with some top hackers earning six figures annually.
Top platforms include HackerOne, Bugcrowd, Synack, Intigriti, and YesWeHack. These platforms host bug bounty programs from companies around the world.
Submit your findings through the platform’s reporting process. Include a clear explanation, proof of concept, steps to reproduce, and any supporting screenshots or payloads.
Yes! Students are encouraged to participate. It’s a great way to build cybersecurity skills, earn rewards, and potentially land jobs or internships in the security field.
Share it with Friends
Follow Me
Your Friendly Hacker
Categories
Use Coupon Code - YFH10
-
Cybersecurity Terminologies – eBook
Rated 5.00 out of 52 reviews₹299.00Original price was: ₹299.00.₹99.00Current price is: ₹99.00. Add to cart -
20 Editable Resume Templates – ATS Friendly
Rated 5.00 out of 52 reviews₹249.00Original price was: ₹249.00.₹99.00Current price is: ₹99.00. Add to cart


Your Friendly Hacker
Lets Secure the World
Join me on my journey to make the internet a safe place again.
Contact Form